Tea App Breach Exposes 72K IDs – Comprehensive Report
The Tea app breach has shattered trust in a platform celebrated for female empowerment—exposing 72,000 user images, including 13,000 ID selfies used for verification, on underground forums like 4chan. This sweeping data leak strikes at the heart of a women‑only safety app, igniting debates about privacy, defamation, and whether digital vigilance has its limits.
This article dives deep into verified reporting on the breach and app functionality, compares trending media coverage, and provides a nuanced view—with fresh guidance for women navigating dating safety in a digital age.
What Is Tea App and Why It Rose to Fame
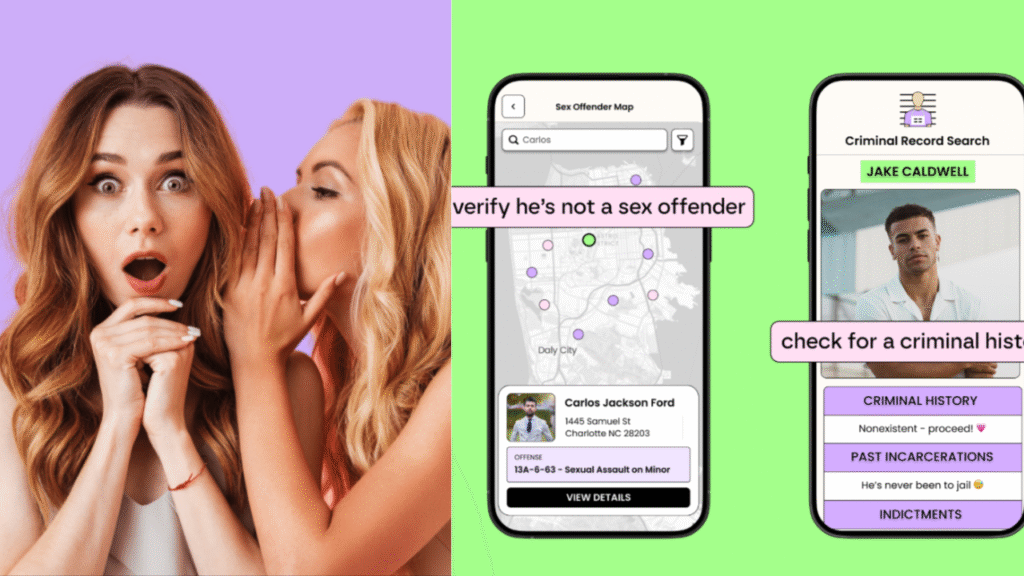
Tea is a women‑only platform launched in 2023 that enables users to anonymously post photos and experiences about men they’ve dated, flagging “red flags” or “green flags.” Featuring tools like reverse‑image search, background checks, and phone‑number lookups, it positions itself as a safety companion to apps like Tinder, Bumble, and Hinge.

The app gained viral popularity in mid‑July 2025 via TikTok and community chatter, climbing to the #1 free app on the U.S. Apple App Store with over 2 million new users requesting access within days. Its official site claims over 1.7 million users and high ratings, underlining its meteoric rise. Tea for Women.
The Breach: How, When, and What Was Exposed
On July 25, 2025, Tea confirmed it discovered unauthorized access to a legacy data storage system, revealing around 72,000 images—about 13,000 verification selfies and ID scans, plus 59,000 images from posts, messages, and comments.
Multiple outlets agree that the compromised files appeared on 4chan, after being first reported by 404 Media. The URL listing the storage attachments was later disabled, but not before public sharing began.
Tea asserts that no email addresses or phone numbers were included in the breach, and only data from users who signed up before February 2024 was affected.
Company Response and Ongoing Investigation
Following the breach, Tea engaged third‑party cybersecurity experts and intensified system security checks. The company insists there is no evidence of current user data compromise and reaffirmed user privacy as its top priority.
An in‑app message from admin “TaraTeaAdmin” informed users of the incident, prompting hundreds of reactions within the community. Business Insider
Privacy and Legal Implications
Tea’s model raises legal and ethical questions. Users upload photos of men without consent. U.S. legal analysis suggests that—as long as the content isn’t used commercially—such uploads are usually defensible under fair use and Section 230 protections. There is no general right in U.S. law to block image use of a person in public settings.
However, attorneys warn that posts can lead to defamation suits or harassment claims, particularly if individuals suffer reputational harm or persistent targeting. FOX 2 Detroit
Additionally, Tea’s screenshot blockade has proven ineffective; users bypass restrictions via secondary devices or screen recorders, leading to further leaks of reviews and information on platforms like X and Reddit.
Community Reactions and Gender Debate
Supporters view Tea as a vital step for women’s safety—a “digital whisper network” enabling shared vigilance that dating apps lacked. User reviews emphasize how Tea helps avoid emotionally harmful or dangerous encounters.
Conversely, critics—especially men—label the platform “digital vigilantism,” warning it can facilitate false accusations, abuse, or misuse under anonymity. Debates on TikTok and forums reflect discomfort over potential bias in crowd‑sourced judgments. HypeFresh
Lessons Learned and Recommendations for Users
For Women Using Tea or Similar Apps:
- Assume verification selfies and IDs may be permanently stored, even post-verification.
- Avoid posting identifiable or defamatory content without clear proof.
- Monitor scanned media or images appearing publicly; some posts have already circulated beyond the platform.
For Data Privacy Advocates and Regulators:
- The breach underscores the need for stronger data retention and deletion policies, especially around sensitive verification files.
- Verification that relies on biometric and identity data should respect minimum retention periods.
- Platforms should conduct regular third-party audits and have breach-response transparency plans.
Conclusion
The Tea app was conceived as a solution for women to date more safely, combining community insight and verification tools. But the exposure of 72,000 sensitive images—including ID‑based verification selfies—on 4chan has turned that narrative upside down. The very data designed to ensure safety became a vulnerability, creating a privacy risk.
This incident illustrates the delicate balance between protecting users and safeguarding their data. Women seeking safety must now navigate heightened risk and uncertainty—and platforms like Tea must rebuild trust, update defenses, and rethink the ethics of anonymity-driven safety measures.
Ultimately, what began as a community-held vision for safer dating has become a cautionary display: cybersecurity must evolve as fast as community trust.
Subscribe to trusted news sites like USnewsSphere.com for continuous updates.





