IT Security Costs and Risks: Evaluating the True Value of Cyber Defense
In today’s digital-first world, businesses face an ever-evolving cyber threat landscape. Understanding the true value of cyber defense is essential for organizations striving to strike the right balance between IT security costs and risks. As cyberattacks grow more frequent and sophisticated, failing to invest in robust cybersecurity measures can lead to catastrophic financial losses and reputational damage.
The Rising Costs of Cybersecurity Breaches
Recent reports reveal that the global average cost of a data breach has reached a record high of $4.88 million, marking a significant increase from previous years. In the United States, organizations face even steeper consequences, with the average breach cost soaring to $9.44 million per incident, according to IBM’s 2024 Cost of a Data Breach Report.

For small and medium-sized enterprises (SMEs), the financial impact is equally alarming. Studies indicate that cyber incidents can cost SMEs an average of $50,000 per attack, a figure that can cripple smaller organizations with limited cybersecurity budgets. These statistics emphasize the urgent need for proactive investment in IT security to mitigate potential financial and operational risks.
Hidden Costs Beyond the Obvious
While direct expenses like remediation efforts and legal fees are apparent, indirect costs often go unnoticed but can be even more damaging. These include:
- Reputational Damage: Loss of customer trust and negative media exposure.
- Operational Downtime: Interruptions that halt critical business processes.
- Regulatory Penalties: Non-compliance fines under regulations like GDPR or CCPA.
Evaluating the ROI of Cybersecurity Investments
Investing in cybersecurity is no longer an option but a necessity for businesses aiming for long-term success. However, how much should organizations allocate to IT security? The Gordon-Loeb Model, a well-regarded economic framework, suggests that businesses should ideally invest up to 37% of the potential financial loss from a cyber breach to achieve optimal protection.
When evaluating cybersecurity investments, consider:
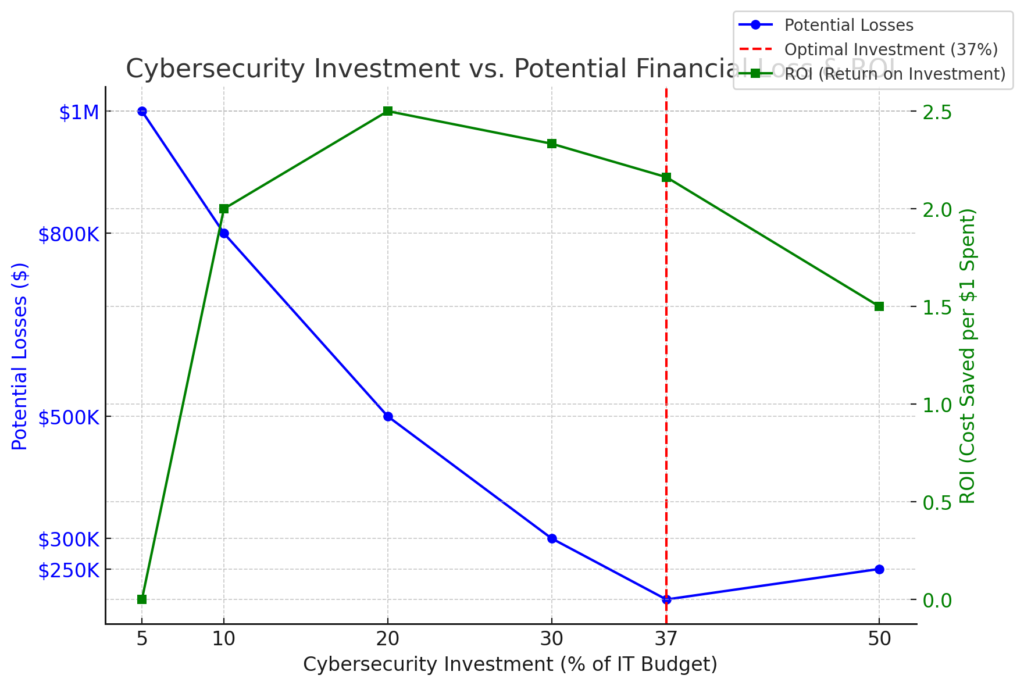
- Cost vs. Risk Analysis: Assessing the likelihood and impact of potential threats.
- Advanced Threat Detection Tools: AI-driven security solutions for proactive defense.
- Employee Training Programs: Educating staff to recognize phishing and other attack vectors.
By conducting a cost-benefit analysis, businesses can better understand how their cybersecurity measures translate into financial protection and operational resilience.
Key Strategies for Effective Cyber Defense
To combat rising cyber threats, businesses should adopt a multi-layered approach to security. Consider the following best practices:
- Implement Zero Trust Architecture (ZTA): Never trust, always verify access requests.
- Regular Security Audits and Penetration Testing: Identify vulnerabilities proactively.
- Cloud Security Enhancements: Secure data in hybrid and multi-cloud environments.
- Incident Response Planning: Develop and test response strategies to mitigate attacks quickly.
Proactive defense strategies, combined with consistent monitoring and timely updates, ensure that organizations remain ahead of cyber adversaries.
Conclusion: Investing in Cybersecurity is Investing in Your Future
Evaluating the true value of cyber defense goes beyond immediate cost considerations. It’s an investment in protecting business continuity, customer trust, and long-term growth. By prioritizing cybersecurity measures, organizations can mitigate risks, reduce potential financial losses, and enhance their resilience in an increasingly volatile digital landscape. [USnewsSphere.com / IBM]








